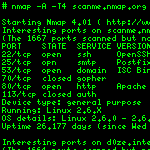
Kalau anda dah tau atau belum, kat internet tu ade satu web site http://www.virustotal.com menjalankan servis untuk menganalisa file-file yg disyaki dan juga menyediakan report yg lengkap dan cepat!! Dengar macam hebat dan memang hebat.. Website ni boleh mengesan virus, worms, trojans, dan segala jenis malware yg boleh dikesan antivirus. (sebab antivirus ni kdang2, jname laen dah detect, die tak detect lagi).. jadi, klau gune website ni, kite leh tau la file tu dah penah di detect oleh antivirus ape saje yg ade kat dunia ni.. klau takde, maknenye file tu selamat...
Menurut website die, virustotal ni:
* Free (tu yg sedap dgr tu)
* Gune pelbagai enjin antivirus
* Virus signature yang paling latest giler.
* Result yg detail bagi setiap antivirus.
* Statistik terkini.
dah sudah merapu, mari kite belajar gune.. tapi cam tkyah ajar sbb cam senang je gune.. tapi tulis jela bagi pnjang sket post kali ni.. lagipun, tak best plak asyik copy paste, tulis sendiri pus sket.. hehe..
1. snang je nak gune.. mule2 bukak je laman web http://www.virustotal.com dan kalau malas nak taip, klik je link tu..
2. Pastu akan kuar page camni..

3. Pastu apa lagi.. kita ramai-ramai klik butang browse dan pilih file yg kita ragui tadi.. pastu klik butang send file.. tu je.. pastu tunngu result.. senang bukan? Tapi perasan tak kat bawah textfield tu ade thickbox cakap "send over SSL", itu function untuk user yg ade masalah nak upload care biase.. macam saye penah kena, mase tu nak upload file kat kampus.. dah name pon file virus, firewall block untuk upload, jadi gune la sendover ssl tu.. dan berjaya upload..
4. Result die rupe camni..

dan ini..

amacam.. seronok tak.. jumpe lagii.. selamat mencuba..
assalamualaikum..